LONDON (Reuters) – U.S. travel management firm CWT paid $4.5 million this week to hackers who stole reams of sensitive corporate files and said they had knocked 30,000 computers offline, according to a record of the ransom negotiations seen by Reuters.
The attackers used a strain of ransomware called Ragnar Locker, which encrypts computer files and renders them unusable until the victim pays for access to be restored.
The ensuing negotiations between the hackers and a CWT representative remained publicly accessible in an online chat group, providing a rare insight into the fraught relationship between cyber criminals and their corporate victims.
CWT, which posted revenues of $1.5 billion last year and says it represents more than a third of companies on the S&P 500 U.S. stock index, confirmed the attack but declined to comment on the details of what it said was an ongoing investigation.
“We can confirm that after temporarily shutting down our systems as a precautionary measure, our systems are back online and the incident has now ceased,” it said in a statement.
“While the investigation is at an early stage, we have no indication that personally identifiable information/customer and traveller information has been compromised.”
CWT said it had immediately informed U.S. law enforcement and European data protection authorities.
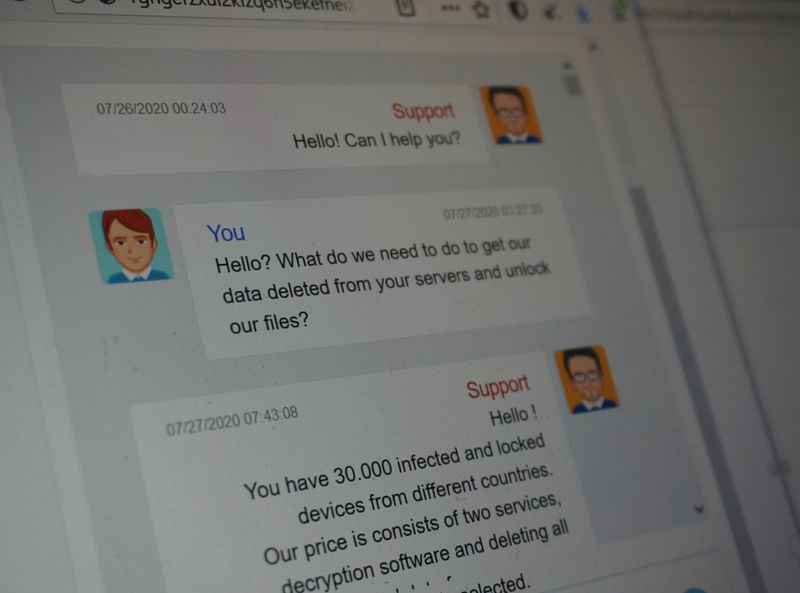
A person familiar with the investigation said the company believed the number of infected computers was considerably less than the 30,000 the hackers told CWT they had infected.
DIGITAL RANSOM NOTE
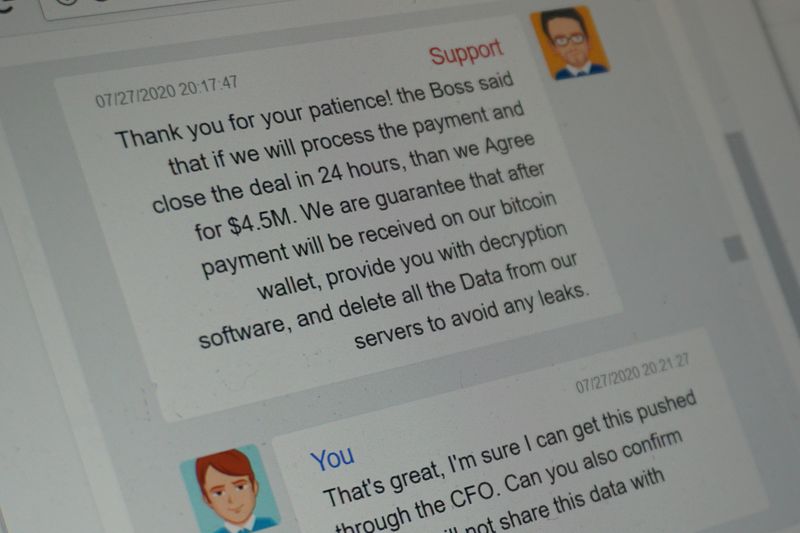
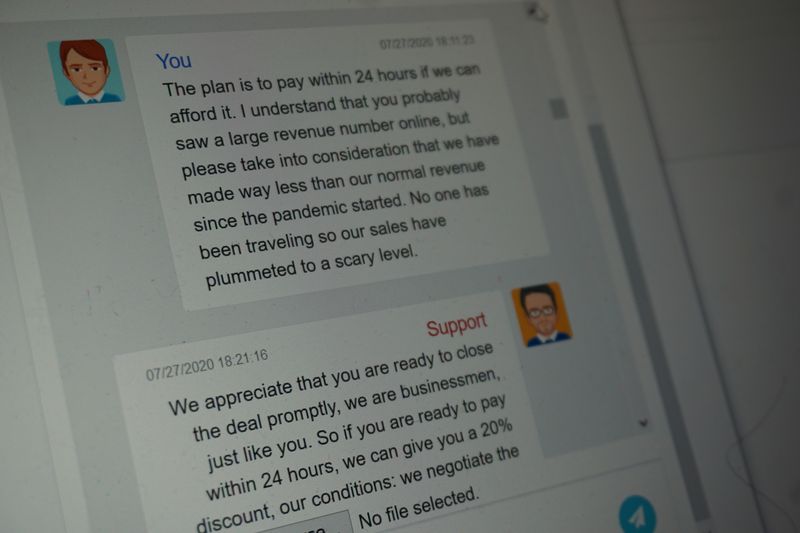
The hackers initially demanded a payment of $10 million to restore CWT’s files and delete all the stolen data, according to the messages reviewed by Reuters. “It’s probably much cheaper than lawsuits expenses (sic), reputation loss caused by leakage,” the attackers wrote on July 27.
The CWT representative in the negotiations, who said they were acting on behalf of the firm’s chief financial officer, said the company had been badly hit by the COVID-19 pandemic and agreed to pay $4.5 million in the digital currency bitcoin.
“Okay let’s get this moving forward. What are the next steps?” the representative said after agreeing to the ransom.
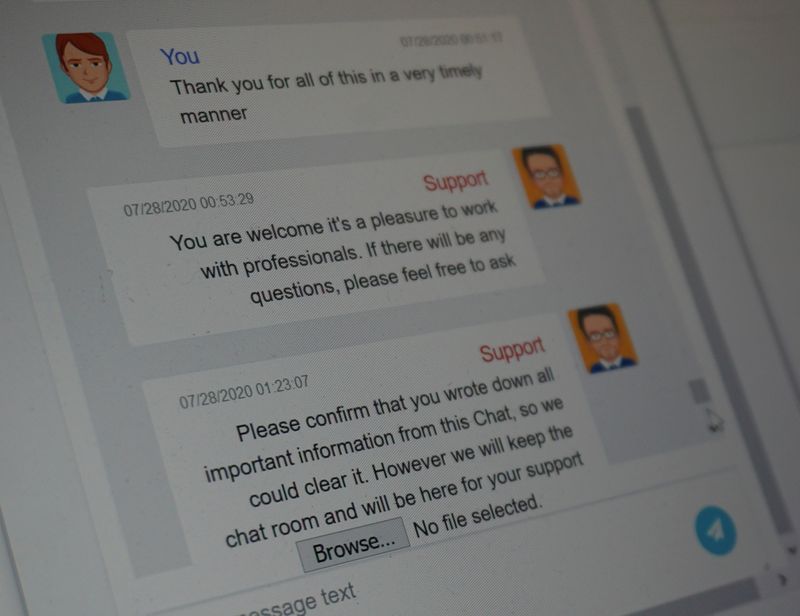
A public ledger of digital currency payments, known as the blockchain, shows that an online wallet controlled by the hackers received the requested payment of 414 bitcoin on July 28.
Messages sent to email addresses used by the hackers went unanswered.
In a ransom note left on infected CWT computers and screenshots posted online, the hackers claimed to have stolen two terabytes of files, including financial reports, security documents and employees’ personal data such as email addresses and salary information.
It was not clear whether data belong to any of CWT’s customers, including Thomson Reuters, was compromised.
Western security officials say ransomware attacks are a consistent and serious threat to businesses and private companies, despite the increased attention usually given to the headline-grabbing antics of state-backed hackers.
Such attacks are thought to cost billions of dollars each year, either in extorted payments or recovery costs.
Cybersecurity experts say the best defence is to keep secure data back-ups, and that paying ransoms encourages further criminal attacks without any guarantee that the encrypted files will be restored.
(Additional reporting by Raphael Satter in WASHINGTON; Editing by Gareth Jones)